Identify your vulnerabilities and calculate your risk.
Beyond day-to -day operational needs, organizations must continuously assess conditions and risk factors and adjust the security program to best meet long-term risk management objectives. In addition to the direct costs of a security program, it is important to calculate avoidable threats and losses, and the costs attached to those potential losses. When these elements are quantified, stakeholders can justify security investments and change drivers.
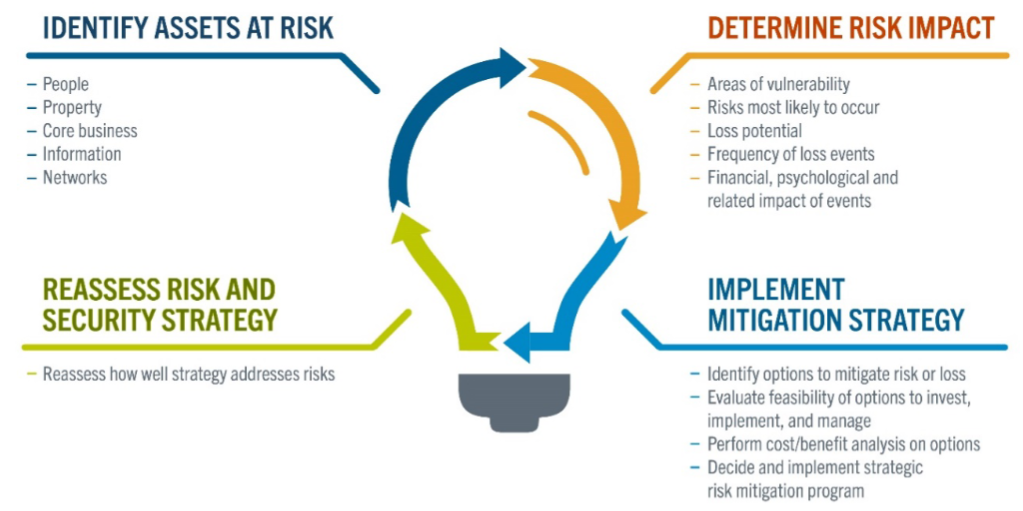
The onus on executive management is to ensure that the security spend generates the highest return on investment, not only the lowest cost. Because risk to organizations can be influenced by a variety of factors and change over time and by location, determining the impact and cost of risk is no small task. It takes resources, time and expertise in risk analysis. To determine what risk is relevant, a thorough risk assessment should be conducted. ASIS General Security Risk Assessment Guideline, © 2003 ASIS International, outlines recommended practices for assessing risk in an organization, summarized in the following steps:
Keeping perception of risk in mind is important when calculating risk. An organization’s integrity and reputation can be as significant to its valuation as physical assets and people, and it is as critical for security strategy to combat perceptions of risk as actual risk, as relates to brand integrity. To demonstrate the significance of public perception, Freedonia Group reports that 61% of people profiled by MRI-Simmons are generally worried about violence and crime, though perceptions of crime are higher than actual. With pervasive issues like assault on nurses in hospitals, violence against women in higher education, growing active shooter risk across the nation and cyber threats to private information, it is a relevant security concern. Outsourcing offers greater flexibility to keep up with these demands as risk trends evolve and change, and provides the resources to backup response needs when events do occur.
If you or your current company are looking to explore the benefits of a contract security solution as a partnership hybrid model or full support please contact us and let us answer any questions you may have. To request more information and download our full report “Evaluating Security Options: A Change Driver for Outsourced Security” please click here.